Identity in a Deregulated IT world
In short: Gianpaolo presents a daring proposition about a deregulated IT. I believe that GP’s idea is a very valid one. In the post below I explore the implications of a world where consumerism is brought to the extremes of IT deregulation: in such a world user centric identity management and user control/consent are key enabling aspects that cannot be ignored.
From time to time I have nice chats with Gianpaolo, during which he gives me glimpses of his thinking about where IT is going. I especially liked his considerations about consumerism and deregulated IT: not that he finally made a post on the topic, I can share some of the trends and implications I draw from it.
The foundation of this entire matter lies in becoming fully aware of the trend that has been dubbed as consumerism. This is already a pretty loaded term already, however I really like the position of Peter Sondergaard (Gartner director of global research), as captured by David Berlind at the Gartner Symposium/ITxpo:
Sondergaard went on to describe how consumer technologies and configurations now rival and often exceed in the prowess of the corresponding technologies found in the organizations that are used to serving consumers on their terms (“their” being the organizational side). “Consumers are rapidly creating personal IT architectures capable of running corporate style IT architectures” said Sondergaard. “They have faster processors, more storage, and more bandwidth. In 2012, expect consumer technologies to be fully incorporated and integrated into all settings (eg: home offices, remote offices, in transit, etc.).
That’s totally true. Months ago I was chatting with my book buddy Garrett, and he was telling me that he just got a wall of 4 22″ flat screens: definitely more than what you can expect on the typical office desk (actually, that reminds me of the TV walls features in Farheineit 451). Hardware availability is just the enabling aspect of the consumerism revolution: the maturity in the use of software is even more widespread. People proficiency with IT systems is increasing at an impressive pace. Just think of DVRs, Media Centers, Tivo, shared printers, routers & access points, USB devices, smartphones, bluetooth configurations, P2P and chat software, aggregators, news portals, seach engines, blog authoring & wikis, social software, GPS Navigators, next gen gaming consoles, cameras, ad so on. That list includes items that are used daily by END USERS! This is stuff that implies intuitive understanding of abstract concepts such as menu hierarchy, drivers, modes, protocol compatibility, storage management, access privileges, time dependent events, credentials, data formats… compare that with the flashing display of the VCR after a power outage that not so long ago was a common sight in households without a teenager! End users not only catched up with company-grade IT systems, they already started to invert the tendency. Think of IM, blogs, wikis and social software… they are now first class citizens in the enterprise, but they started as end user tools. As more and more digital natives enter the scene (again see Sondergaard) you can expect the trend to accelerate, and the emergence of consumption models that are today hard to imagine for digital immigrants (twitter, anyone?).
This new maturity empowers users to use their own resources for doing more things, and it also makes them much more independent. Things like Windows Update and the innovations in the OS security & robustness take care of maintaining a (reasonably, for the scenario) reliable baseline even without the an IT department. This of course requires the user to take more responsibilities than he was requested in the past: blowing up a machine you use for work because you installed a cracked software with a trojan as a surprise becomes much more costly.
In this situation, it is obvious that user centered identity management is of paramount importance. As the user accesses assets online, an easy and safe way of propagating his or her identity becomes a cornerstone of the entire system. As the interactions become more complex, the control on what is propagated must increase proportionally. The awareness of what information is being disclosed, and the subsequent decisions about consent, requires a level of sophistication that can be delivered today by user experiences such as CardSpace Identity Selector. When complex business transactions always happened between two companies, the details of what indentity information would be exchanged were buried in the partnership agreements between the two enterprises. When the user himself is in control of his own business decisions, and partnerships are created and dissolved in the space of a single transaction, those details MUST emerge to the user’s attention.
As the users became more demanding, the quality of the services offered on the web followed suit. Instant Messaging and Web mail are two examples of publicly available services that reached a high level of reliability. Gianpaolo’s interesting idea (any mistakes and misinterpretations are all my responsibility, please refer to the original post for getting the point in his own words) is that a brave CIO could deregulate his company’s IT, that is to say “make all your IT division-offered services compete with external market offerings. In this scenario central IT becomes only one of the many service providers, you (business unit / empowered ex-central-IT-constrained customer) can choose from.” That would mean, for example, offering to your department managers the choice of hosting the mailbox of their employees on Exchange or on Hotmail. Such an approach would provide an unprecedented capability of differentiating the offer, allowing to size the resources more closely to the actual needs. Example: a manufacturing company has knowledge workers in HQ, subsidiaries and factories. Those KWs handle a substantial amount of mails; furthermore, they have a very dynamic schedule and the need to organize meetings all the time. They obviously need a full fledged mailbox on the company’s exchange. Then there are shift workers, who work on the production floor and follow a fairly rigid schedule. They own an account on the company network, as they need to authenticate when they operate certain machinery, but the potential mail traffic and scheduling needs are not enough for justifying the maintenance cost of a full fledged Exchange account. As a result, all sorts of alternative methods are used: corkboards, word of mouth and so on. In a differentiated IT world, the shift workers could be provisioned with an Hotmail account. That would give the level of service that is truly required by the job function, and more, without burdening the company with the costs of doing the same on premises. The entire thing should be arranged, naturally: an hotmail account should be provisioned programmatically in the context of the company business processes, the alias should be tracked and maintained in the suitable DLs, ad so on… Again, it’s not that IT is not needed: all the “usual” considerations about leveraging SaaS apply here as well (and again GP’s blog is really a good place to keep an eye on it).
Gianpaolo goes ahead and makes some business considerations, likening the IT deregulation with some other big deregulations the industry has seen in other sectors (national telcos going private, to name one). The paragon holds on many aspects: as the economy of a country matures, the capability of private initiatives to compete for offering base infrastructure services increases. The push to open a new market outgrows the initial needs of a young country, where the infrastructure had to be supplied by the only entity powerful enough to take on the task. I am not so sure that the analogy can be taken verbatim, since here the pressure seems coming from the governance itself (cost saving) and the contractual power of the users (as opposed to the citizens) seems much weaker. However it’s some time that I don’t think in abstract business term, so my opinion counts like the two of spades when you’re playing soccer (feel free to ignore the last 14 words:-) ).
There are many ways in which the above is made possible by the consumerism. The user must be somewhat proficient and independent for making the above truly feasible: public services are resources that your IT does not control. Furthermore, those are services that can be accessed from outside your company network: that will probably open up your workflows, to encompass scenarios where the location from which services areconsumed or offered becomes more and more transparent.
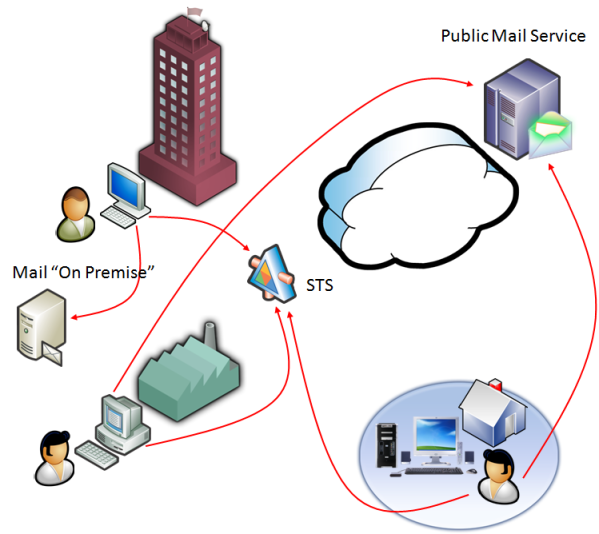
This has a HUGE impact on how your employees handle their identity. Yes, I mean what I wrote. THEY handle their identity. You can provision them with identities which represent aspects of the employer-employee relationship, and you can create the enabling infrastructure for using those identities: you can also create business rules that will deny expressing that relationship (read: issue a token) in contexts you don’t deem appropriate. But operatively, it is the employee that must be empowered to choose when to disclose, what to disclose and to whom. Any other hand-keeping mechanism just adds to the costs and dampen the agility. The idea is that once you’ve set the rules, and the identification machanism is transparent enough, the network of trust and the user awareness should be enough to keep all interactions in the realm of the intended and legitimate. Let’s be more pragmatic and consider again our Hotmail example, adding some cardspace sauce. By choosing an email service from the cloud, you “outsourced” part of your mailboxes management. However, that does NOT imply that you outsourced account management. You want that email account to be part of your processes, and you probably want to be able to deprovision it once the employee leaves the company (otherwise he may keep participating in workflows until you update the entire IT system: you’d have a “lack of federation” problem with yourself :)). In order of doing so, you may create a system where your employee accesses the external mail service by presenting a token issued by an STS of yours (nevermind that today’s hotmail would not allow that, that’s in line of principle). Your employee would be allowed to use the mail, but not ADMINISTER it. You would also be able to specify to the service what are the defining claims of your employee, and the employee would have control over it (cardspace would show them). Those claims, and the token itself, would be the perfect mechanism for maintaining an agile relationship with the service provider. Just imagine what it could mean for billing! The service may recognize the signature of your STS as coming from a company enlisted in a certain public registry, and just log the call: at the end of the month it may send you a combined bill without even ever had any explicit contract! Naturally, that’s SF for now: more probably, for the first phases of public service integration there will be a classic federation relationships. Since we said that the employee would have a network account, we may authenticate RSTes with Kerberos: employees would be able to get a token seamlessly only when accessing the services from the company intranet. Enabling access from outside the company would be straighforward: it would be just a matter of adding another endpoint to the STS, this time with a policy imposing an authentication factor suitable for external usage (like the contactless smartcard used for accessing the factory building, for example). Consumerization will make that approach more and more feasible. Such a model would still save the company the costs of mantaining a mailbox on premise, without giving up the access control over it just as any other company asset.
Well, that’s very early thinking: I believe that this new concept is going to enjoy a lot of attention in the near future. Yet another trend that will need user centered identity federation for fully realize its potential. I’ll be watching with great interest 🙂

2 Comments