Year’s end blabbering: Omnidirectional Identities

On the Paris-Seattle flight, coming back after 2 weeks spent stuffing myself with all sorts of food with the excuse “after all, you can’t find this in USA” 🙂
Before hurling myself back in the vortex of daily work, and celebrate the end of the year with something crazy, I want to take some time writing down some hallucinatory (=vision without execution) thoughts about omnidirectional identities. Be warned, this may be just pointless rambling at this point. Few weeks ago I chatted about this in front of a microphone with John Udell, digressing along a crazy tangent instead of answering his questions about the book (I eventually came back to Earth and answered properly :)). I don’t know if he’ll deem those fragments publication worthy, but just in case I’ll make a brain dump here. It’s not that there’s much more to do in this small seat anyway (just finished the latest Eco. He didn’t mention underbite at all, I’m happy).
Looking back at the activities related to identity in the past year, I am glad to report that amazing progress has been done. Something that makes 2007 very different from 2006 is the kind of work that was made: in 2007 the accent was on execution. The vision behind the metasystem is still being explored, sure, like Kim’s series on linkage or the discussions about display token and first law demonstrate; and I feel that conjugating the metasystem and claims in enterprise environment is an area that still need focus (especially in fighting old forma mentis that would prevent the full expression of the potential of the new paradigm). However, it is enough to keep an eye on Mike’s blog to get a feeling that the key player rolled up their sleeves and started incorporating the principles of the metasystem in products and offers. Moving from groundbreaking to consensus work mode changes the mix of tasks & roles involved, hopefully freeing some energy for expanding the work of visionaries to new problems and challenges.
Here there’s what imho is one of the most promising area of growth for the mission of identity think tanks: omnidirectional (or multidirectional) identities management. So far the focus has been on studying and “getting right” transactions in which a subject is empowered to use his identity in unidirectional fashion. That’s to be expected, since that is exactly where the problems lie with traditional technologies (I mainly mean passwords, for the friends at home that are tuning in only now. May I suggest a mean to catch up?;) (full disclosure: I’m involved in it)). Frankly, it’s also where the money lies. Solving phishing and identity theft by fixing the unidirectional identity sharing practices (some may say it would be easier to say “authentication”, but I beg to differ) means saving big bucks and increased confidence in the medium, hence the well deserved focus.
Omnidirectional identity is an entirely different animal. Well, sort of. The laws predict and regulate omnidirectional identifiers behavior very well; to name an example, CardSpace takes significant steps for leveraging the omnidirectional identifiers of IPs and RPs for helping the subject to perform server authentication tasks and take informed decisions. The point is that so far we didn’t talk much (if at all?) about omnidirectional identities for subjects. I am not talking about pedestrian application of PKI (“here, take this certificate + private key; use it for identifying yourself with everybody and stop bugging me”). I am thinking more of dynamically issued, authority endorsed, free-form identifier. The difference I have in mind is much like issued vs primitive tokens; the former can be issued as part of the transaction itself, as opposed to the latter that must be “in place” before the ball starts rolling (ie: saml vs x509 tokens. *Please* don’t tell me that X509 certificates are tokens themselves, David knows the effect it has on me:)).
The canonical example I use for an omnidirectional identity (can I use OI from now on?) is the MySpace or Facebook page of somebody. It clearly carries identity information (read: claims), but its dynamics escape the canonical Subject/IP/RP triad known interactions. Think about it! Let’s say you’re a friend of mine in Facebook. You sign in in the Facebook website, you go to the list of your friends and you see my entry; when you click on it, you obtain some info about myself (the ones I chose to share with my friends) and you see the latest silly things I did or write. Or let’s say you are NOT a friend of mine, but you are a Facebook user; you can still obtain a set of my identity information (albeit more limited) and even some pictures if I am in Andy Warhol mode.
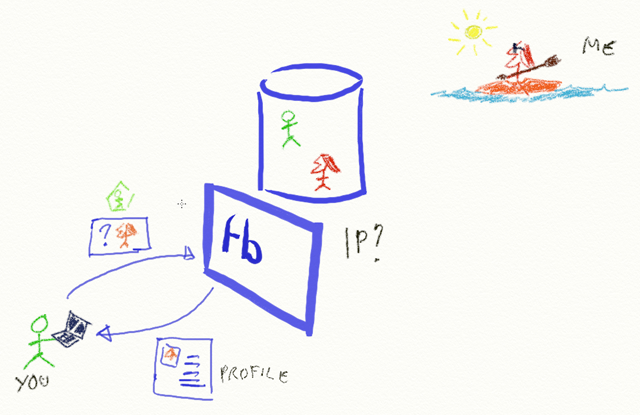
Fig 1: An interaction in which you require my facebook profile, which shows important differences from the usual S/IP/RP case. Here facebook is the IP, sure; but you are requesting my identity, not yours; you are not requesting it for complying with the requests of an RP; and the entity referenced by the claims you’ll obtain (that would be me) may not even be online at the moment of the transaction
Let’s decompose the above using the roles we are familiar with. Facebook is the IP, few doubts about it. You are clearly the subject, since you are the one driving the transaction. But! The identity you are requiring is not your own! You are requiring MY identity! And yet, I may even not be online in that very moment; bizarre, eh? And who’s the RP? Not facebook, since it already has that info; is it you?
In traditional S/IP/RP, the identity that gets exchanged is in fact requested and issued in order to comply with certain requirements (the RP wants to know your age or similar). Here we don’t observe a similar purpose; you are just requiring access to data and it seems just an accident that the information happen to be an identity (read: I don’t even know if we should use a token in the traditional sense for carrying it). In fact, from the exquisitely technical perspective we can disregard the semantic of the data requested and fold back on the traditional model. In that case Facebook would be the RP: it would authenticate you at signin time, and once you request something it would authorize you and give you appropriate access levels to the data you require (my profile) regardless of the kind of data requested.
The point is that we simply cannot ignore that the data exchanged represent identity information: if we do, we risk running into situations like facebook beacon (background here). The Laws still hold, of course, but we need to do some steps and spell out in practice some solid guidelines about how user consent can be applied in this scenario, what are the responsibilities of the roles in this space, what happens when omnidirectional revert to unidirectional & vice versa, etcetera. And of course it would be interesting to explore B2B possibilities such as how profiles can be shared/transformed across different entities (ie: is it interesting to have facebook and linkedin providing simply different views of a single identity?). IMHO it would be great to get a big brain like Kim thinking about it, and try to understand the underlying rules of that extended realm of identity management.
Social networks are the en vogue reason for digging deeper in OIs, but it’s far from being the only one. Less obvious situations come from the traces we leave on the internet in general, and the consequences that they can have on us. How common it is to search the name (or the mail alias) of somebody in the context of a hiring process, in a sort of homebrew background check? Usenet, forums, search engine caches contain traces of our activity all the way back to the 90’s; or at least it may seem so. Few months ago the identity woman’s identity debacle highlighted how brittle & prone to polluting that system is, for the simple reason that it’s not a system. It is simply an emergent property of those tools, which naturally never spent any cycles in verifying that the name you use for posting on newsgroup is really yours. Polluting the results of those alleged background checks is far easier than setting up google bombing schemes, but unfortunately that does not really erode their credibility and may severely influence opinions & decisions. I’m no privacy expert, but I foresee that the twitter & facebook generation will gladly give up some privacy and accept to imprint some identification in every online activity (hence emptying of all credibility those activities that, not holding any certification, can be forged) in exchange of preserving their reputation. And it sounds like an OI would be one of the best candidate tools for helping in this area. How? It’s all to be discovered 🙂 The list of situations in which people may benefit from an algebra of OIs could go on and on, just think of contact management as it is done today (you’d be surprised by how many times people confused information cards with vcards, and the mess that derives by trying an explicit cast).
So far I implicitly referred to activities driven by people; in fact, I believe that we’d benefit in including the identity of things in this bigger picture as well. The absolutely incredible progress we witnessed in the last few years in the field of synthetic image generation may already today invalidate pictures or videos as evidence, or at least it will be so once we will go beyond the possibility of forgery detection. And the staggering amount & universal availability of image & sound acquisition devices may soon require some way of certifying in a secure way what is the true source of a clip (think some institution doctoring a video of making a certain point, then freeing it on youtube or soapbox). This idea was already expressed years ago by some Gartner analyst, and I believe we are getting there faster than they thought (pretty common pattern nowadays); what I would add, in light of all we said before, is that I think it would be criminal to develop practices & technologies specifically for the identity of things, instead of including those in the context of what we already learned about the identity of people. At this point we have seen that we build silos only for tearing them down few years later, and it isn’t cheap; we should probably aim to build directly an open space 🙂
The identity metasystem brought a forma mentis and a valid tool for solving an important problem that was screaming for a solution. Exploring those new areas with the same attitude won’t be easy. The Laws arise also from observing the failure of many former attempts in the last few years, and they help protecting from attacks that evolved & stabilized into well defined forms & genus (phishing anyone?). The need for a public identity on the net is somewhat more recent, hence there’s more speculation and less observation data; for the same reason, the pressure on doing deeper work on the subject may not materialize right away. Eventually, I hope that we will spend some cycle on that; thanks to our experience in fixing the unidirectional case, this time we have our chance as an industry to get this right at the first shot.
Well, if you read all the way to here I have to compliment you for your incredible patience! As a token of gratitude, I’ll explain what’s the meaning for the picture on top; it’s a morphing of my Chinese signature, made with a stone seal & scanned, into the smartpox that points to this blog. The first one was used for signing documents (hence in pretty unidirectional transactions), while the latter is intended to be printed on labels and left around to be read by special sw on phones with cam (hence as omnidirectional as it can get).
Happy new year everybody!

Do you think law 4 serves any purpose other than to determine who goes first in the “show me some ID” dance?
Hey Now Vibro,
OI huh? interesting blabbering.
Thx 4 the info,
Catto