WIF and the ASP.NET Sign In Processing Pipeline
At the end of the 1st day of the WIF workshop I typically go through a pretty deep session about WIF object model. Although somebody may accuse me to be a sadist to impose such a heavy topic at the end of a very intense training day, in the last 3 workshops this turned out to be OK; I want you to first experience what you can do with WIF before getting here, otherwise you may think that everybody need this level of detail and in fact that’s absolutely not the case. Personally I went this deep only because I wanted to document it well in the book and for the workshops themselves, even writing the training kit and the samples didn’t require all this. In fact, this session is typically appreciated by people who come to the workshop with pre-existing knowledge of WIF, as they usually never dive this deep by themselves.
Since apparently there’s no *detailed* representation of the WIF pipeline on the web, I am posting a tasting sample of the workshop here. Remember, all the workshop slides and the videos of the Redmond sessions will eventually be available in the training kit & channel9. But for the time being…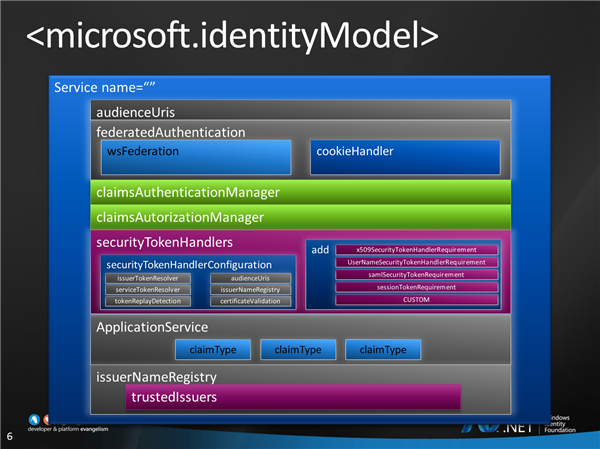
Above you can find is a concise representation of the Service element of the microsoft.identityModel WIF config section. I use it to highlight why it is useful to know about the WIF pipeline; many of the elements there make sense only if you know what classes will process which requests, at what time and in which order.
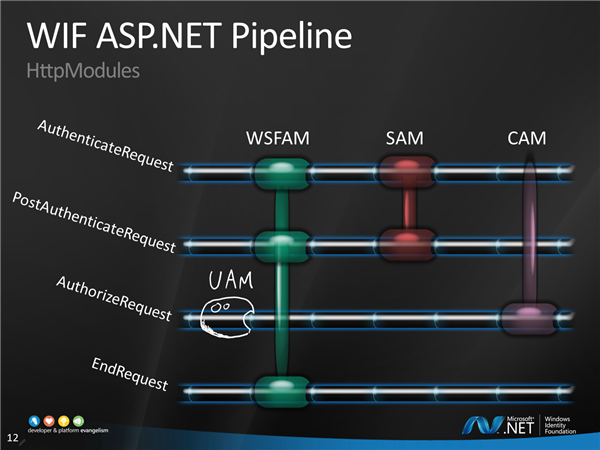
Processing a request for a resource on a web site protected by WIF is kind of a pinball game through ASP.NET and WIF-specific HttpModules. Here my tablet pen comes in useful for tracing the flow:-) the representation above has the advantage of clarifying both the activation sequence and the responsibilities (ie events handled) by the various modules. All implementations in the first, unauthenticated GET are so simple that I just talk though that.
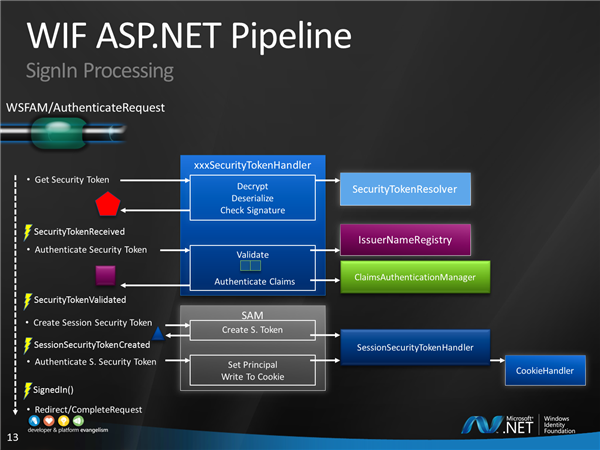
What’s less simple is the processing of the token coming from the STS. The slide you see above is fully animated, no human (apart from Dominic, of course :-)) would be able to take this as a whole… here I pretty much walk attendees through the various stages, introducing the various classes as they come into play. Getting people to stay alert during this is the kind of challenge that every entertainer dreads, but it can indeed be fun :) 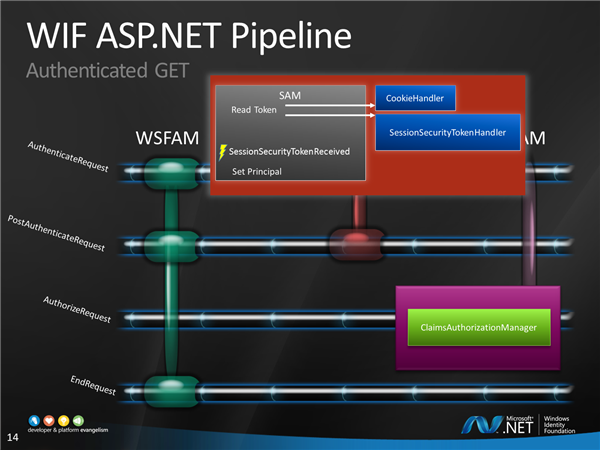
Finally, here there’s the last leg in which the request is coming in with the session cookie.
Well, imagine adding a lot of details and step by step description, and that’s it. That’s a small tasting sample of what you get on the workshop and (with less colors but a lot more words) with the “Programming Windows Identity Foundation” book. Of course it’s not all like this, there are many architectural moments which show you how to attack problems with the claims-based approach and those are not product-specific… I like to keep things interesting 🙂
We may still have (very!) few seats left for Singapore and Redmond if you click on the links real fast… hope to see you there! 😉

This is great.
Can not wait to attend the session.
I am having issues in forcing the login expiration time from WIF.
cookieHandler/persistentSessionLifetime for forcing login expiration does not seem to work.
Thanks
dhamija_dinesh@hotmail.com