Requesting an AAD Token with a Certificate – without ADAL
I am sure you have seen the exciting news about daemon apps & O365 that Alex shared a couple of days ago.
That post reinvigorated interest in the token request flow based on certificates. We have a complete end to end sample giving you step by step guidance on how to implement that flow with ADAL .NET, but we don’t yet have detailed protocol documentation for it.
We will get to it, but in the meanwhile: if you need to reproduce the same flow in a different platform, a good trick is to run the e2e sample and observe a trace of the traffic it generates. To give you a headstart, here there’s a breakdown of the token request it generates – mildy formatted for your screens:
POST https://login.windows.net/contoso.onmicrosoft.com/oauth2/token HTTP/1.1
Content-Type: application/x-www-form-urlencoded
client-request-id: a2ef0cd8-60e5-4620-ac66-6f2a344e075b
return-client-request-id: true
Host: login.windows.net
Content-Length: 986
Expect: 100-continue
Connection: Keep-Alive
resource=https%3A%2F%2Fcontoso.onmicrosoft.com%2FTodoListService
&client_id=82692da5-a86f-45c9-9d53-2f88d51b478b
&client_assertion_type=urn%3Aietf%3Aparams%3Aoauth%3Aclient-assertion-type%3Ajwt-bearer
&client_assertion=eyJhbGciOi[…a lot of stuff…]-j5UBo1A
&grant_type=client_credentials
The main things to notice here:
1) it’s a POST to the token endpoint
2) it is a client_credentials grant, as expected
3) you need to specify as client_assertion_type the magic value urn:ietf:params:oauth:client-assertion-type:jwt-bearer
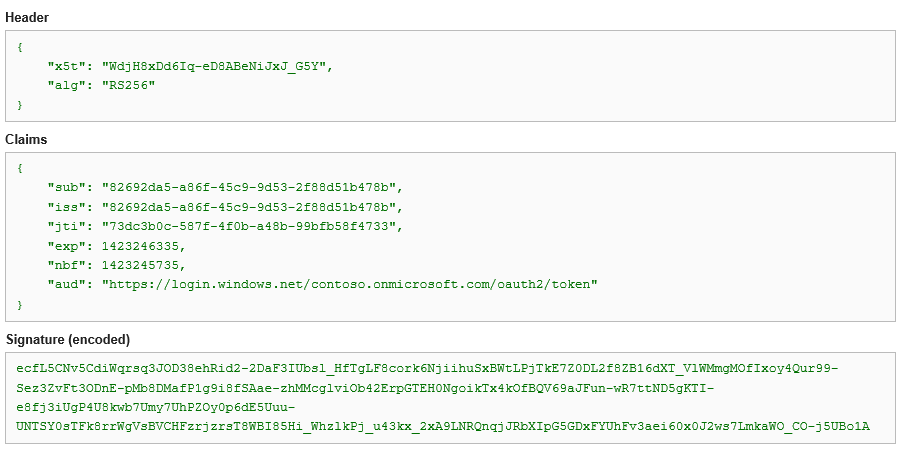
The other thing of interest is in the client_assertion itself, which is the artifact in which the certificate actually comes into play: it’s an assertion you need to create and sign with the certificate you registered as credential for your application. ADAL does this for you, ut if you want to work directly at the protocol level you’ll have to do it yourself. Here there’s how the JWT of the assertion looks like, as decoded by Google’s JWT decoder.
Things to notice:
1) As this is signed with a certificate, the algorithm is RS256
2) subject and issuer are the same – the identifier of the client! ![]()
3) the assertion is scoped to the token endpoint, its intended destination
That’s it! It should be really straightforward for you to use any JWT library on your favorite platform to produce the above. Have fun! ![]()