Windows Identity Foundation Tools for Visual Studio 11 Part IV: Get an F5 Experience with ACS2
Welcome to the last walkthrough (for now) of the new WIF tools for Visual Studio 11 Beta! This is my absolute favorite, where we show you how to take advantage of ACS2 from your application with just a few clicks.
The complete series include Using the Local Development STS, manipulating common config settings, connecting with a business STS, get an F5 experience with ACS2.
Let’s say that you downloaded the new WIF tools (well done! ![]() ) and you at least checked out the first walkthrough. That test stuff is all fine and dandy, but now you want to get to something a bit more involved: you want to integrate with multiple identity providers, even if they come in multiple flavors.
) and you at least checked out the first walkthrough. That test stuff is all fine and dandy, but now you want to get to something a bit more involved: you want to integrate with multiple identity providers, even if they come in multiple flavors.
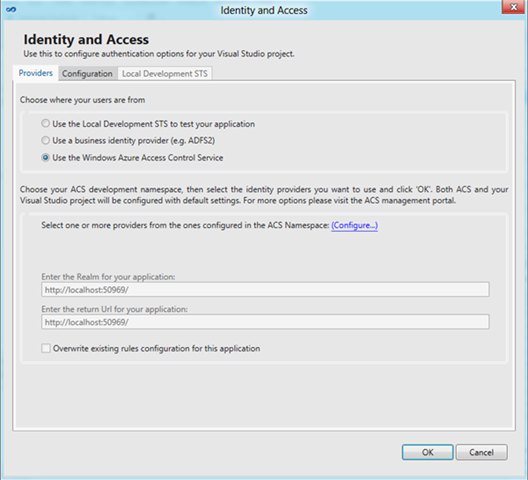
Open the WIF tools dialog, and from the Provider tab pick the “Use the Windows Azure Access Control Service” option.
You’ll get to the UI shown below. There’s not much, right? That’s because in order to use ACS2 form the tools you first need to specify which namespace you want to use. Click on the “Configure…” link.
You get a dialog which asks you for your namespace and for the management key.
Why do we ask you for those? Well, the namespace is your development namespace: that’s where you will save the trust settings for your applications. Depending on the size of your company, you might not be the one that manages that namespace; you might not even have access to the portal, and the info about namespaces could be sent to you by one of your administrator.
Why do we ask for the management key? As part of the workflow followed by the tool, we must query the namespace itself for info and we must save back your options in it. In order to do that, we need to use the namespace key.
As you can see, the tool offer the option of saving the management key: that means that if you always use the same development namespace, you’ll need to go through this experience only once.
As mentioned above, the namespace name and management key could be provided to you from your admin; however let’s assume that your operation is not enormous, and you wear both the dev and the admin hats. Here there’s how to get the the management key value form the ACS2 portal.
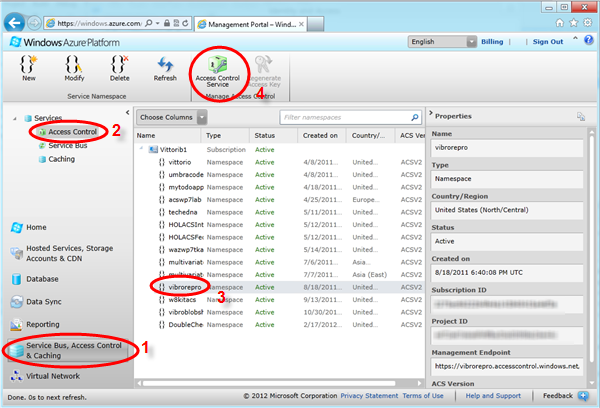
Navigate to http://windows.azure.com, sign in with your Windows Azure credentials, 1) pick the Service Bus, Access Control and Cache area, 2) select access control 3) pick the namespace you want to use for dev purposes and 4) hit the Access Control Service button for getting into the management portal.
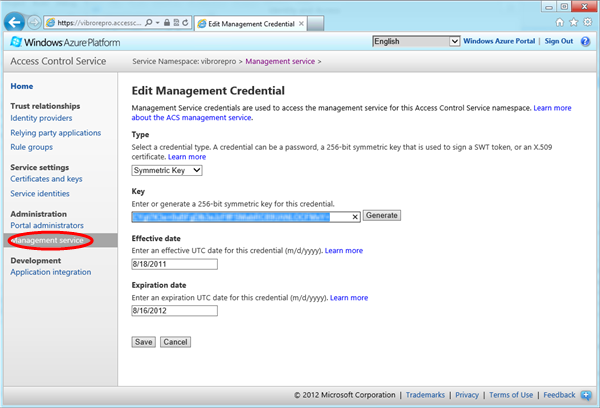
Once here, pick the management service entry on the left navigation menu; choose “management client”, then “symmetric key”. Once here, copy the key text in the clipboard (beware not to pick up extra blanks!).
Now get back to the tool, paste in the values and you’re good to go!
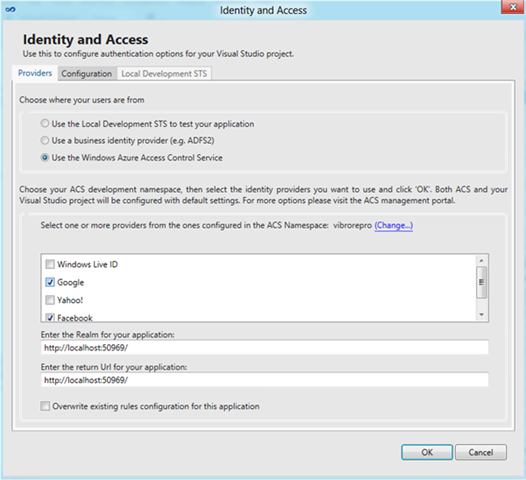
As soon as you hit OK, the tool downloads the list of all the identity providers that are configured in your namespace. In the screenshot below you can see that I have all the default ones, plus Facebook which I added in my namespace. If I would have had other identity providers configured (local ADFS2 instances, OpenID providers, etc) I would see them as checkboxes as well. Let’s pick Google and Fecebook, then click OK.
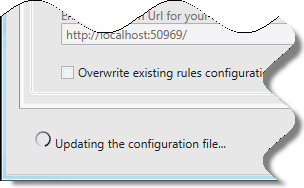
Depending on the speed of your connection, you’ll see the little donut pictured below informing you that the tools are updating the various settings.
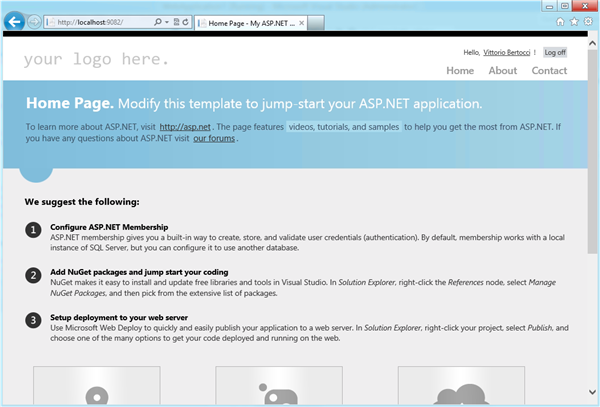
As soon as the tool closes, you are done! Hit F5.
Surprise surprise, you get straight to the ACS home realm discovery page. Let’s pick Facebook.
Here there’s the familiar FB login…
…and we are in!
What just happened? Leaving the key acquisition out for a minute, let me summarize.
- you went to the tools and picked ACS as provider
- You got a list checkboxes, one for each of the available providers, and you selected the ones you wanted
- you hit F5, and your app showed that it is now configured to work with your providers of choice
Now, I am biased: however to me this seems very, very simple; definitely simpler than the flow that you had to follow until now ![]()
Of course this is just a basic flow: if you need to manage the namespace or do more sophisticated operations the portal or the management API are still the way to go. However now if you just want to take advantage of those features you are no longer forced to learn how to go through the portal. In fact, now dev managers can just give the namespace credentials without necessarily giving access to the Windows Azure portal for all the dev staff.
What do you think? We are eager to hear your feedback!
Don’t forget to check out the other walkthroughs: the complete series include Using the Local Development STS, manipulating common config settings, connecting with a business STS, get an F5 experience with ACS2.





Great article and walk thru! It’s great to have the WIF stuff integrated with VS2012 and Windows8 now.
I would point out that the pain points I experienced were:
1. Getting the WIF tooling via the VS Tools..’Extensions and Updates’. Search for ‘Identity and Access Tool’
2. Not having the MVC4 Web Project properties set to .NET 4.5 (no ‘Identity and Access’ right click menu available if runtime is < .NET 4.5)
3. Trying to authenticate with ACS using the wrong symmetric key (use the Management Service/Management Client key, NOT the one in Certificates and Keys) 🙁
Even with the above, it was still much easier than it has been in the past to get a working test project using Federated Identity! Bravo to the team!!
Thank-you so much for this post!! I was finally able to get ACS working in VS2012.